And in countries where Tor use is flagged or monitored, that’s already a red flag. They don’t know what you’re doing, but they know you’re doing something. On that note, if you’re having trouble telling the two apart (including their strengths and weaknesses), check out our comparison of Tor and VPNs. While Tor does a solid job anonymizing your traffic, there are still gaps, and that’s exactly where a VPN steps in. Not just to stay anonymous online, but to stop your ISP, government, or even opportunistic creepers from tracking your every move.
NordVPN – Best VPN For The Dark Web Overall (via Free Trial)
By using a VPN to connect to Tor — a special browser designed to access the dark web — you can securely access the dark web using a technique known as Tor-over-VPN. Tools like Tor anonymize users by masking their IP addresses, but this doesn’t make them invisible. Use trusted resources to find safe sites and stay aware of the risks involved.
Unlike Tor, however, it cannot be used to access the public internet. Additionally, Tor exit nodes are often blocked by websites that don’t trust them, and Tor over VPN can’t do anything about that, either. A logless VPN, which doesn’t store any traffic logs nor session logs is highly preferable. Your ISP only sees the encrypted VPN traffic and won’t know you’re on Tor. All your device’s internet traffic first goes to the VPN server, then bounces through the Tor Network before ending up at its final destination.
How To Access The Dark Web Safely And Anonymously

You can access these websites without worrying about someone snooping on a Tor exit node, offering more private browsing of what is known as the deep web. The Tor Browser (“The Onion Router”) is a product of the Tor Project, which was founded on the belief that “internet users should have private access to an uncensored web.” If you are reading this, you’ve likely heard about how the Tor Browser can help protect your internet privacy and anonymity online. Initially designed for secure military communications, it evolved into a broader tool for online anonymity, later expanding to public use with the Tor network. The dark web presents various threats, including malicious software and computer viruses, posing risks to users' systems and data security.
Connect To A VPN Before Opening Tor
That said, the Tor Browser and a VPN make an excellent team for protecting your online activities from prying eyes, and provide optimal online privacy protection. A secure VPN server slows down your browsing much less than the Tor Browser and also opens access to geo-blocked local content around the globe. A VPN keeps all of your online activities – including your web browsing, online gaming, streaming, and file-sharing – undercover and safe from being tracked or recorded.
Step 4: Boot Into Tails OS From The USB Drive

However, there are several “.onion” search engines like “onion.city”, “onion.to”, and “notevil” that you can use to find suitable marketplaces. Obviously, since these websites don’t show up in the Google search engine, it can be a relatively hard task to find them. But, if you are planning to do more than just browse Tor sites and, for example, you plan to purchase goods via the Tor network (for your own good, stick to the legal stuff), it’s important to take some extra precautions. Since you’ve now installed the Tor browser, you can safely browse dark web websites and other (previously) hidden websites.
Don’t Use Your Main Device
Many sites on the dark web are scams, and some host illegal content. This makes it harder for websites, ISPs, or surveillance tools to see who you are or what you’re doing. You’ll know you’re on the dark web when the URLs end in “.onion” — these addresses only work inside the Tor network.
Navy and released to the public in 2004, Tor is favored for its unmatched security and privacy features. Here’s a brief guide on how to safely access the dark web and some tips for using it. It bounces traffic through several servers before delivering it to its destination, making it harder to track a user’s activity or location. Also known as The Onion Router, TOR enables users to browse the Internet, including the Dark Web, anonymously.
Silk Road was one of the first dark web marketplaces and it allowed users to trade multiple types of nefarious goods and services, including weapons and identity fraud resources. Darknet markets facilitate transactions for illegal goods and services. Other dark web search engines include Not Evil, Torch, Haystack, and Ahmia. DuckDuckGo’s no-track dark web search service can be accessed in the Tor browser and is an excellent resource for information about the dark web.
Step 2: Download And Install Tor Browser
Download Tor from its official website at torproject.org. Tor routes your traffic through a chain of relays to obscure your IP address. Think of your email inbox, banking dashboard, cloud documents, subscription content, or internal business tools. These pages are open to everyone and don’t require any special tools to access.
- One option is to try DuckDuckGo’s .onion version, which is great for privacy.
- In the U.S., dark web usage has been growing steadily—not just among cybercriminals, but also among privacy-conscious users.
- You won’t be able to search the dark web with a regular browser (such as Chrome or Firefox).
- The Tor network routes your internet traffic through a series of encrypted nodes, providing anonymity and privacy.
Combining both provides extra security. Tor anonymizes by bouncing traffic through relays; VPN encrypts and routes through a single server. It disables JavaScript and other potentially risky web features for maximum security. Combining it with VPN and good digital hygiene improves security. Tor provides strong anonymity but is not 100% foolproof. Tor encrypts your traffic and routes it through multiple volunteer-operated relays, making it difficult to trace.
Ahmia consistently delivers accurate results and makes it easier to browse without accidentally stumbling onto disturbing or harmful content. It organizes links by category, like forums, email services, blogs, and file-sharing tools, which makes browsing easier and more efficient. Keep in mind that this isn’t an exhaustive list of dark web sites.
Dark Web Tools And Services
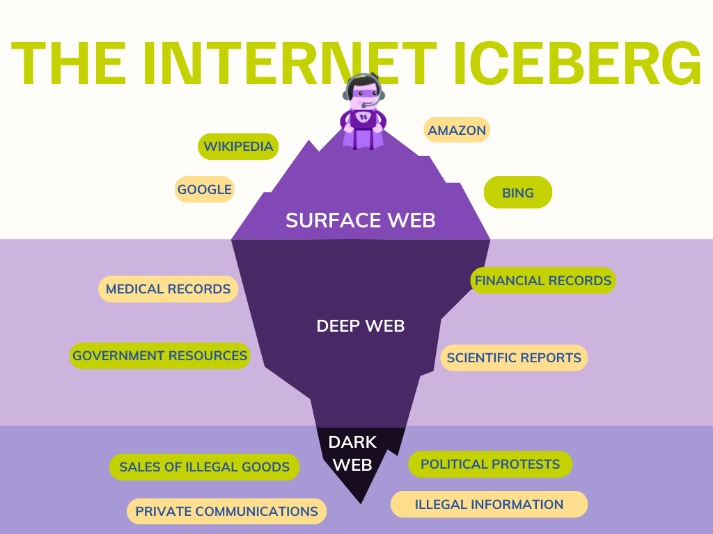
The Deep Web includes unindexed content like private databases and password-protected sites accessible with standard browsers. The dark web contains a range of content, some of which is illegal, including marketplaces for drugs, weapons, stolen data, and other illicit services. When you must visit the dark web, you should exercise extreme caution and avoid accessing illegal marketplaces or engaging with disturbing or extreme content. It hosts encrypted websites, often used for privacy, anonymity, or illicit activities. On the other hand, the deep web is the hidden part of the Internet that contains private or restricted content that is not indexed by search engines.

The dark web offers a marketplace section where users can buy legal or illegal products. Importantly, not all deep web content is illicit; much of it is benign and essential for everyday online activity. Unlike the public “surface web,” dark web sites are deliberately concealed and require specialized software to access, the most well-known being the Tor (The Onion Router) browser. He strives to make complex cybersecurity topics accessible and understandable to the broadest audiences. With over 15 years of experience in content creation and digital publishing, he knows how to craft informative, useful content, with thorough research and fact-checking to back it up. One of the challenges of exploring the dark web is that you can’t just use a search engine and type in what you’re after like you would on the surface web.
Common Security Mistakes To Avoid
Other sites explicitly block search engines from identifying them. Whereas the deep web is the part of the web not searchable by traditional search engines and requires special tools to access it. You can access it with regular web browsers and search engines.
Clario Anti Spy’s Data breach monitor scans for known breaches tied to your email and alerts you if anything’s been exposed. Before you explore further, check if your data has already ended up on the dark web. Here’s how to access the dark web safely.
Many turn to the dark to grab such medications with their private and secure networks. Some common pain relievers and sleeping pills available in the EU are illegal in various Middle Eastern and Asia countries. Such sites include blogs, gaming sites, social media, and super-encrypted email platforms. As much as the Darknet contains even the “good” stuff, it’s not a place you need to stumble about blindly without proper dark web safety.



