
Imperva DSF flexible architecture supports a wide range of data repositories and clouds, ensuring security controls and policies are applied consistently everywhere. While risky and requiring strict operational security, cyber HUMINT gives defenders access to information not available through passive monitoring alone. While using anonymity tools like Tor is not illegal, engaging with criminal networks or transactions is. Some countries restrict access to anonymity tools altogether, while others monitor them closely for signs of criminal behavior.
Why Can’t You Use Google On The Dark Web?

Terrorist groups have used the dark web since its inception due to its anonymity and lack of regulation. Traditional social media platforms such as Facebook have also created versions that work with the dark web to provide services across all dimensions of the World Wide Web. Ross Ulbricht, the creator of Silk Road, was arrested on suspicion of hiring a hitman to kill six people, but the charges were later dropped. The indie game Sad Satan was claimed to have been found via the dark web, but inconsistencies in the reporting cast doubt on the story.
The Internet Of Things: When Everything Becomes Smart
There you will see the security level in the ‘Security’ section. Tor Browser is the most commonly utilized application to access the dark web. NordVPN is our #1 recommendation for dark web browsing because of its security, privacy, and performance.
Knowing what attackers are buying, selling, or planning can guide the creation of threat models and inform security controls tailored to real-world risks. These insights allow security teams to better align their defenses with actual threats. Studying activity on the dark web gives defenders insights into how threat actors think and operate.
Many social media platforms keep their presence on the dark web, and it is no surprise that Facebook has a .onion portal. It allows you to search for images, maps, files, videos, social media posts, and more. SearX is a metasearch engine that you can use on the clear web and dark web. However, that part of the internet is unfiltered, so you might encounter unpleasant conversations.
Method II – VPN Over Tor
- For a number of technical reasons, it’s much faster and more reliable than Tor.
- Also, you need to use a privacy-focused browser such as the Tor network to connect via nodes and proxy servers, which are more secure and aim to anonymize traffic requests.
- This adds extra protection since opening Tor itself encrypts your traffic.
- There are several whistleblower sites, including a dark web version of Wikileaks.
- These sites aren’t just important resources; they’re like lifelines used to serve readers living under oppressive regimes.
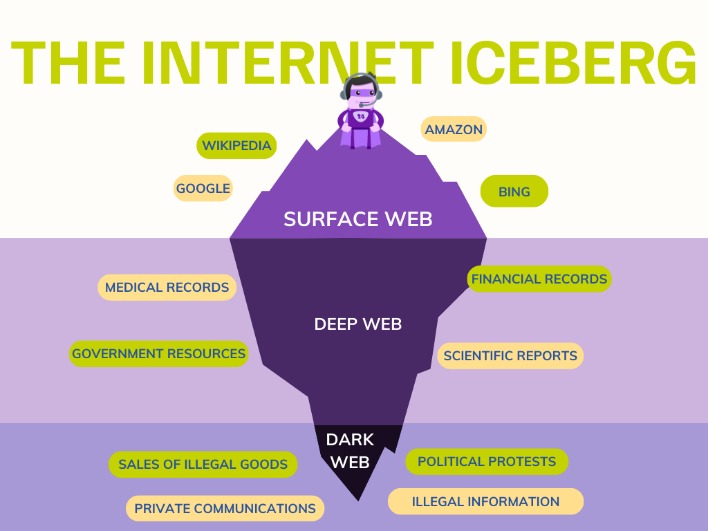
These are publicly accessible pages that can be found using standard browsers without any special configuration—ranging from news websites and eCommerce platforms to social media networks and informational sites. It comprises websites and resources indexed by search engines like Google, Bing, or Yahoo. The Deep Web refers to any material that is not searchable, such as online banking and email, premium service services, and academic databases. A virtual private networking (Proxy server) is just a great way to hide your online identity as well as your place whilst allowing you to access the internet securely. Choosing a reputable VPN service provider is important, and be aware that some Dark Web websites may block access to VPN users.
Can Cybersecurity Teams Use The Dark Web To Track Threats?
Similarly, people in countries with strict internet access and usage regulations must use Tor clients or virtual private networks (VPNs) to access some public websites. Cybercriminals exploit its hidden nature to operate marketplaces, forums, and services that are inaccessible through traditional search engines. The dark web is notorious for hosting marketplaces that deal in illegal goods and services, such as drugs, weapons, counterfeit money, stolen data, and even human trafficking. Because VPNs offer users anonymity and mask their actual location, they’re also effective tools for accessing geo-locked services.

If your information has been compromised, then it’s likely that your phone number is also on the dark web. One of the great things about Tor is that it can be used to access both the dark and surface web. Connecting to the Tor network might raise eyebrows depending on who and where you are. Note you should use a separate browser than the one you normally use to help ensure anonymity.
VPN Over Tor
Unfortunately, some oppressive regimes have figured out a way to block Tor traffic. One of the major advantages of using Tor in overly-restrictive countries is that it keeps your online travels private. Check out my article for more information about the dark web and how to access it while staying safe. This is why I strongly advise anyone visiting the dark web to exercise the greatest of caution during their dark online travels. It is also used to facilitate human trafficking, money laundering, and worse. It serves as a way for activists to organize gatherings and other activities in secret, with no worries about giving their plans or position away to the authorities.
Top 10 Best Dark Web Search Engines In 2025 Safe &
- Whether you’re a privacy enthusiast or simply curious, always prioritize your online security and remember that not everything on the dark web is safe or legal.
- This is because Tor traffic is usually unencrypted when it passes through the exit node.
- Designed to be hidden from conventional search engines like Google or Bing, the dark web is a portion of the internet.
- Only access the dark web with both a VPN and the Tor Browser active.
- Just remember, this only hides your browser-based activities and doesn’t hide any of your other online activities.
However, third parties such as the government and your internet service provider (ISP) can see that you are using Tor. Since the dark web is a hidden and uncontrolled part of the web, there is a high amount of malware infections present there. The best step is to always disconnect immediately, report the incident to officials through anonymous channels, and avoid interacting any further.
For example, when you sign in to your healthcare provider's portal to view test results or request prescription refills, you're accessing the deep web. Deep web content includes academic research papers, court documents, or medical records. The top layer is referred to as the clear or “surface web,” which is what you're accessing while reading this article. Even in an era of increased online surveillance, the average person on the internet likely has too much to lose to bet on their safety for curiosity's sake. It’s the side of the internet that’s used for transactions and conversations that need to stay anonymous. However, conducting criminal activities via the dark web is illegal.

Step 7: Browse The Dark Web With Tor
Check around with other users and ask if they know anything about the new marketplace. In combination with that data, and data gathered by other methods and/or tactics may in fact lead to complete exposure and could eventually lead to the police standing at your doorstep. If the product or service you’re attempting to buy is illegal, you’re running the risk of arrest. There’s a significant risk to dark web users of being exposed to malware (malicious software) infections. These high levels of anonymity increase the opportunity for the “bad guys” to sell drugs, stolen IDs, credit cards, weapons, and many more compromised products or information.
Use trusted resources to find safe sites and stay aware of the risks involved. They rely on it for anonymous, secure communication to avoid surveillance or censorship. The dark web is used for a variety of purposes, both legal and illegal. In one of the most famous examples, the FBI took down Silk Road, one of the largest illegal marketplaces to ever exist.
How To Access The Dark Web On Your Device

Websites and pages in the deep web might include password-protected content, private forums, and personalized resources. You could consider the clear or surface web the "top" and visible layer of the internet, easily accessible using a browser such as Safari, Chrome, Edge, or Firefox. Here's everything you need to know about this other internet, as well as how to access it.



