
Privacy and anonymity are the core values of the dark web, and it hosts both harmless activities and illegal content. The dark web isn’t only about illegal activities; its primary purpose is to provide maximum anonymity by making your connection private online through encrypted servers. This hidden part of the web carries several illegal activities, including drug and weapon dealing, pornography, private data, and more.
- On the other hand, the dark web hosts marketplaces and forums where illegal goods and services—such as drugs, weapons, and stolen data—are traded, making it a hotspot for criminal activity.
- For this reason, users should be cautious when using their browsers.
- Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity.
- Though a large volume of traffic visits on the open web every day, it only represents 4% of the content on the internet.
- A common misconception about the internet is that, once you open google, you can access anything and everything available online.
The Hidden Wiki & Co

When using Tor, your traffic will never reach its intended destination directly, as it would on surface web browsers. Accessing the dark web is easier than you might think – all you need is an onion and a bit of know-how… To access the Dark Web, you have to use a browser called Tor, also known as The Onion Router. Everything from social media data to medical records are held on the deep web, as is all your email information. Instead, you'd have to go to the local council website and use their internal search engine to find it. But if you want to find something that isn’t a link – a planning document from a local council archive, for example – a google search won’t really help you.
Tor Over VPN Vs VPN Over Tor: Which Should You Use?
Best of all, it’s jargon-free, personalized, and easy to use. Having said that, sometimes, it’s best to steer clear of the dark web entirely. For instance, did you know you can unknowingly break the law while browsing the internet? Clario Anti Spy’s Data breach monitor scans for known breaches tied to your email and alerts you if anything’s been exposed. Before you explore further, check if your data has already ended up on the dark web. Here’s how to access the dark web safely.
PRIVACY ALERT: Websites You Visit Can Find Out Who You Are
Put simply, the deep web is all the information stored online that isn’t indexed by search engines. Again, we can’t emphasize enough that security and anonymity are paramount to those on dark websites. A handful of dark web search engines that do index .onion sites include NotEvil, Ahmia, Candle, and Torch. Obviously, finding these .onion websites is the first challenge, as they won’t show up in Google search results. Dark net websites are called “Tor hidden services“, and they can be distinguished from normal websites by their URLs.
How To Choose The Right Dark Web Monitoring Tools For Your Business?
Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). Hence, you never know when a popular .onion site is going to vanish, or even die. The US Navy’s main reason for creating Tor was to help informants relay information safely over the internet. This .onion link makes it impossible for hackers to impersonate your profile.
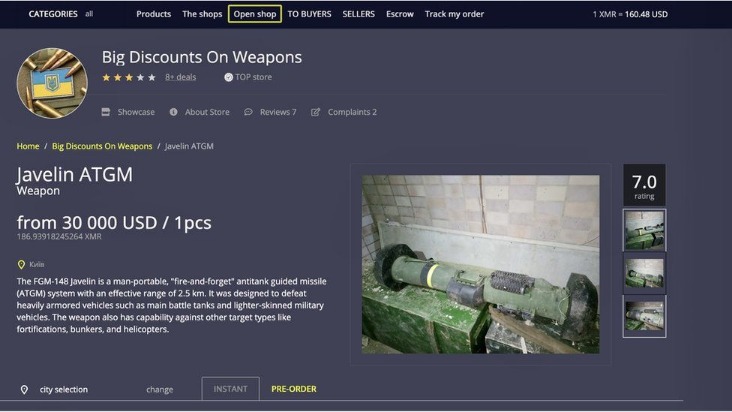
Illegal Content And Explicit Material
The dark web is a small, hidden subset of the deep web that requires special tools to access. Unlike the publicly accessible surface web, the deep web includes sites requiring login credentials but is still accessible via traditional browsers. Estimates suggest around 43% of dark web content and activity is legal, but finding it requires a specialized dark web search engine. The dark web is content that exists on dark nets, which require specialized software (like the Tor Browser), configurations and authorization to access. This can include medical records, research papers, private forums, and networks.
Waqas is a cybersecurity journalist and writer who has a knack for writing technology and online privacy-focused articles. In that case, the government might flag and monitor you even if you’re not a participant or trader. However, a slight action or a wrong click on some websites can land you in deep trouble. Some of the best dark web search engines include Grams and The Hidden Wiki. Although dark web search engines are available, keeping pace with their constant evolution is challenging, even for the best programmers. Therefore, you need a specific dark web search engine known to provide top-notch security and privacy.
The US Naval Research Laboratory developed The Onion Routing (Tor) project in the late 90s. For example, you can find information unavailable to the public and share data privately while protecting your online identity. However, you can find legitimate content and activities here, too.

Is The Dark Web Actually Anonymous?
Law enforcers can use custom software to infiltrate the dark web and analyze activities. In fact, there are growing concerns about law enforcement monitoring what is happening on the dark web. Government authorities across the globe are taking over many Tor-based sites. Some services are genuine; you can get what you want at an agreed fee.
Especially for those who do not have skill in protecting themselves online. Tor can also run off a USB flash drive, is portable, and comes with a preconfigured browser to protect your anonymity. Though there are several ways to access the dark web, Tor is the most widely used method.
Beyond Tor: Other Darknets
While Tor lets you reach .onion sites, many require invitations, passwords, or verification. Many people use it for privacy-focused communication, whistleblowing, or accessing restricted information in censorship-heavy regions. The dark web is not exclusively used for illegal activities. However, while visiting the dark web itself isn’t against the law, engaging in illegal activities there is. Cracking down on many illegal marketplaces on the dark web is the result of such monitoring. You might visit the dark web seeking anonymity or unique services, but this anonymity also attracts scammers.
Despite its negative reputation, not all activity on the dark web is malicious; some users rely on it as a tool for freedom of expression or to circumvent restrictions. These sites can be used by both hackers and individuals looking to exploit vulnerabilities. Drugs are typically sold using cryptocurrency to maintain anonymity, and the buyers and sellers are often difficult to trace. These services are used to obfuscate the origins of cryptocurrency transactions, making it harder to trace them. These are platforms where leaked or stolen data, including personal information, passwords, and credit card details, are bought and sold.
How It Works: Tor Over VPN
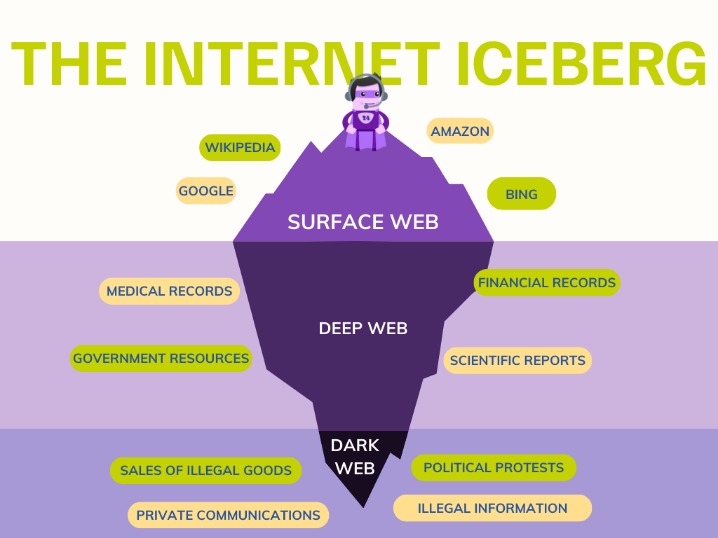
Because of these privacy features, the dark web remains a hidden but active part of the internet ecosystem. The dark web operates on specialized networks that require unique software to access, such as Tor (The Onion Router). These markets operate similarly to physical drug markets but are hidden from law enforcement through the use of the Tor network. The Dark Web is also known for hosting illegal and explicit content, including child exploitation material, snuff videos, and other highly disturbing or illegal material. These sites bypass copyright protection and may be accessed only on the Dark Web to avoid legal scrutiny.
Download Tor from its official website at torproject.org. Tor routes your traffic through a chain of relays to obscure your IP address. Think of your email inbox, banking dashboard, cloud documents, subscription content, or internal business tools. These pages are open to everyone and don’t require any special tools to access.
Hacking Services And Groups
With your VPN active and Tor installed, you’re now ready to connect. Whether you're a journalist, a privacy advocate, or just curious, this guide will walk you through how to access the dark web safely and responsibly. Please check your local laws to ensure your use of VPN complies with statutory requirements.



