
High-profile markets sometimes close overnight, and new markets surge to enormous levels of popularity in no time. We can only hope that the current largest and oldest markets will retire with honor. We have seen several markets fail, bust, exit scams.
AI-generated Fake News Sites: How Artificial Intelligence Is Weaponizing SEO For Profit

Privacy-focused users should choose Sklad with Monero-only and mandatory PGP. Dedicated devices for darknet access provide strongest security. Avoid mentioning markets, vendors, or orders on social media, messaging apps, or email. Never use cryptocurrency purchased with personal information directly on darknet markets. Understanding and implementing proper OPSEC practices is essential for safe darknet marketplace usage. DDoS attacks represent constant threats to darknet markets.
Table Of Contents
- With 256-bit AES encryption, this platform enforces its two-fold service of secure messaging and zero logs of your activity.
- By acknowledging that services, communities, and security measures are in constant flux, you can better position yourself to respond effectively.
- Quality vendors appreciate informed buyers and provide helpful responses.
- Developers, journalists, educators, and advocates for privacy use onion sites as a means to share information in a way that is free and secure.
- Make payments exclusively through cryptocurrencies and avoid vendors or platforms that don’t support anonymous transactions.
Russian Market active since around 2019 is a popular dark web data marketplace that, despite its name, operates primarily in English and serves a global user base. It filled the vacuum left by AlphaBay’s 2017 takedown and quickly grew by absorbing users from other markets that shut down. Below we dive into the top 7 dark web marketplaces of 2025, detailing what they offer, how they operate, their scale, security features, and any notable takedown or status updates. They operate as hidden sites on the Tor network accessible via .onion URLs and use cryptocurrencies like Bitcoin and Monero for payments.
- While Tor offers anonymity on the dark web, your online activities leave breadcrumbs that can reveal your identity.
- Customer satisfaction guaranteed on all gold jewelry purchases.
- Keep an eye on cybersecurity news, dark web community announcements, and trusted information sources to learn about new scams, exploits, or social engineering methods.
- A VPN encrypts the data traffic and keeps your activities private on the dark web.
- Security teams are investing in dark web monitoring tools to spot early warning signs of breaches.
WarpZone Marketplace
Discover the hidden layers of the internet with our comprehensive guide to the best dark web links and onion sites in 2025. Look for markets with strong reputations, verified vendors, and positive user feedback. Yes, these markets prioritize user security with advanced measures like encryption, PGP key authentication, and escrow systems. By exclusively accepting Monero (XMR) for all transactions, the platform prioritizes anonymity and security for its users.

Top 5 Dark Web Marketplaces
These campaigns helped them gain users and redirect traffic after attacks such as DDoS. The dark web is not easily accessible, especially with browsers like Chrome or Safari, as it requires specialized protocols like Tor’s onion routing. It was created in 1999 as a secure communication platform for people and groups working on liberatory social change. Due to law enforcement, many markets now require invites, referrals, or verified PGP identities. You can also use its .onion link via the Tor network to access the site in restrictive countries, where it might be unavailable.
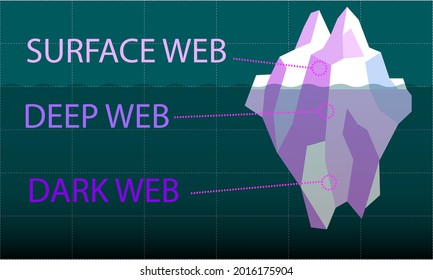
Our team searched the dark web and put together a list of the most active dark web marketplaces in order to assist you in monitoring illegal trade of products, cybercrime activity, and dark web trends in the dark web space. Monitoring these trends, knowing where stolen data is being traded, and understanding how these markets and search tools operate can help preempt threats. These markets sell a range of illegal goods and services, including drugs, weapons, stolen data, and counterfeit items, and they typically require special software like Tor for access. Although some of these markets prohibit certain extreme content such as violence or exploitation, most operate with very few rules beyond ensuring the security and anonymity of their users. Dark web markets are like hidden online stores, except instead of selling clothes or technology, they specialize in illegal products and services. Dark web marketplaces are hubs where vendors sell everything from digital tools to physical goods.
Law Enforcement Tactics And Market Resilience
With its nifty “conjoin” feature, users can combine different coins in one transaction, covering the user’s tracks and maintaining their anonymity. We ensured that the dark web sites we chose had reviews and feedback from real users on other forums; this way, we can be sure of the site’s reliability and legitimacy. Threat actors can execute highly targeted and scalable attacks with minimal effort as more tools become accessible and easier to use. It's a solution that scans hidden sources, such as dark web markets, hacker forums, and Telegram channels, for specific keywords or company assets.
In addition, they have a referral and reward system, so if you bring in more users, you get a share. Each of these “bots” represents a compromised device, and prices for access range from $3 to $10, depending on the quality and freshness of the data.However, it works by invitation only and is accessed through several mirrors on the Tor network. Despite some occasional service issues, Russian Market remains a favorite among cybercriminals seeking fresh access and financial data. To access all its features, you need to make a minimum deposit of between $40 and $100.Among its tools are a BIN checker (for verifying cards) and a cookie converter, ideal for those looking to move quickly. You won't find drugs here, but you will find tons of credentials, RDP access, CVVs, and records stolen using malware.The platform works with data collected by well-known malware such as Lumma, RedLine, Raccoon, Vidar, and Aurora.
Tweak Tor Browser Settings
These platforms provide cybercriminals with anonymity, making it difficult to track and stop illegal activities. The forum is notorious for its role in facilitating unauthorized access to networks and distributing malware. Operating on both the dark web and the surface web, Exploit.in serves as a hub for malicious actors seeking to buy and sell exploits, malware, and stolen data. Since its creation in 2014, it has become known for providing an extensive database of hacking tools and resources. XSS is primarily focused on hacking, corporate access, and data leaks, making it a hub for cybercriminals and hackers.
Formerly known as Archive.is, it is one of the best onion sites on the dark web. The downside is that it limits data to only 25mbps per user. RiseUp is a top dark web website that offers secure email services and a chat option.
Anonymity is one of the main reasons people explore dark web links, but it’s surprisingly easy to compromise your identity if you’re not careful. Avoiding these dangers means staying informed, sticking with trusted directories, and never trusting a .onion site just because it looks polished. These often include links to malware-infected downloads, phishing sites, or scam forums. But instead of protecting whistleblowers, these fakes are designed to collect sensitive documents or deanonymize users through malicious code.
Products And Services

Combined with Tor's onion routing, TLS creates multiple encryption layers protecting user traffic. PGP encryption protects sensitive communications including shipping addresses from market administrators and potential attackers. Cryptocurrency transactions create permanent blockchain records potentially linking users to purchases. Weak markets suffer from predictable session tokens, insufficient timeout periods, or 2FA bypass vulnerabilities.
The Fall Of Silk Road And The Rise Of New Marketplaces
It offers over 20,000 listings ranging from narcotics and forged documents to hacking software and fraud tools. By 2025, it is already a key player for those involved in the business of data theft and trafficking. It is entirely focused on financial cybercrime and offers much more than just stolen cards or basic logins.Here you will find malware logs, remote access (RDP), brute force accounts, complete identity packages, and access to financial platforms. With constant updates and new providers entering the market, Exodus is positioning itself as a major player in the digital underworld of credential theft.



